Today, many businesses are turning to secure web apps to ensure their customers’ data stays protected. If you’re someone with a knack for tech and entrepreneurship, it’s crucial to grasp how these secure web apps work to earn your customers’ trust, whether it’s their credit card details or even the name of their beloved pet.
Let’s start with the basics – web application development services. These services are essential in creating secure pathways for data to travel safely online. But building secure web apps is not as simple as adding an SSL certificate and calling it a day. It involves detailed planning, specialized skills, and ongoing attention to safety measures.
Now, let’s dive into how secure web apps help safeguard customer data.
The Magic of Encryption: Turning Data Into Code
Encryption is one of the primary methods used by secure web apps to protect sensitive information. Think of encryption as turning your message into a secret code that only the sender and the intended receiver can read. As data travels across the web, it’s transformed into unreadable text that only specific decryption keys can make sense of. Essentially, it acts like a digital lock.
Technologies like SSL (Secure Socket Layer) and TLS (Transport Layer Security) are commonly used to create secure connections between web servers and browsers. So, when you enter your password or credit card info, these technologies spring into action. The data gets encrypted before it even leaves your device, ensuring that cyber intruders are left puzzled.
Using encryption is crucial and should be an initial step in any plan for developing secure web applications.
These are just a few of the layers involved in building secure web apps that safeguard customer data, creating trust and loyalty in the digital age.
Authentication and Authorization: Who Gets In and What Can They Do?
Imagine authentication and authorization as the security team at a digital event. They decide who can enter and what they can do once inside. For secure web apps, these processes are essential in keeping customer data safe.
Authentication: The Virtual ID Checker
Authentication is all about confirming a user’s identity before allowing access to sensitive data. Here are some common methods:
- Passwords – the classic way to verify identity
- Biometrics – using unique physical traits like fingerprints or facial recognition
- Multi-Factor Authentication (MFA) – This method adds extra security layers, such as sending a code to your phone alongside the usual password, greatly minimizing the risk of unauthorized entry.
Authorization: Setting Limits
Once a user is authenticated, authorization determines what they can access. It ensures that users, whether employees or systems, can only reach the information necessary for their tasks, which helps to prevent data leaks or breaches.
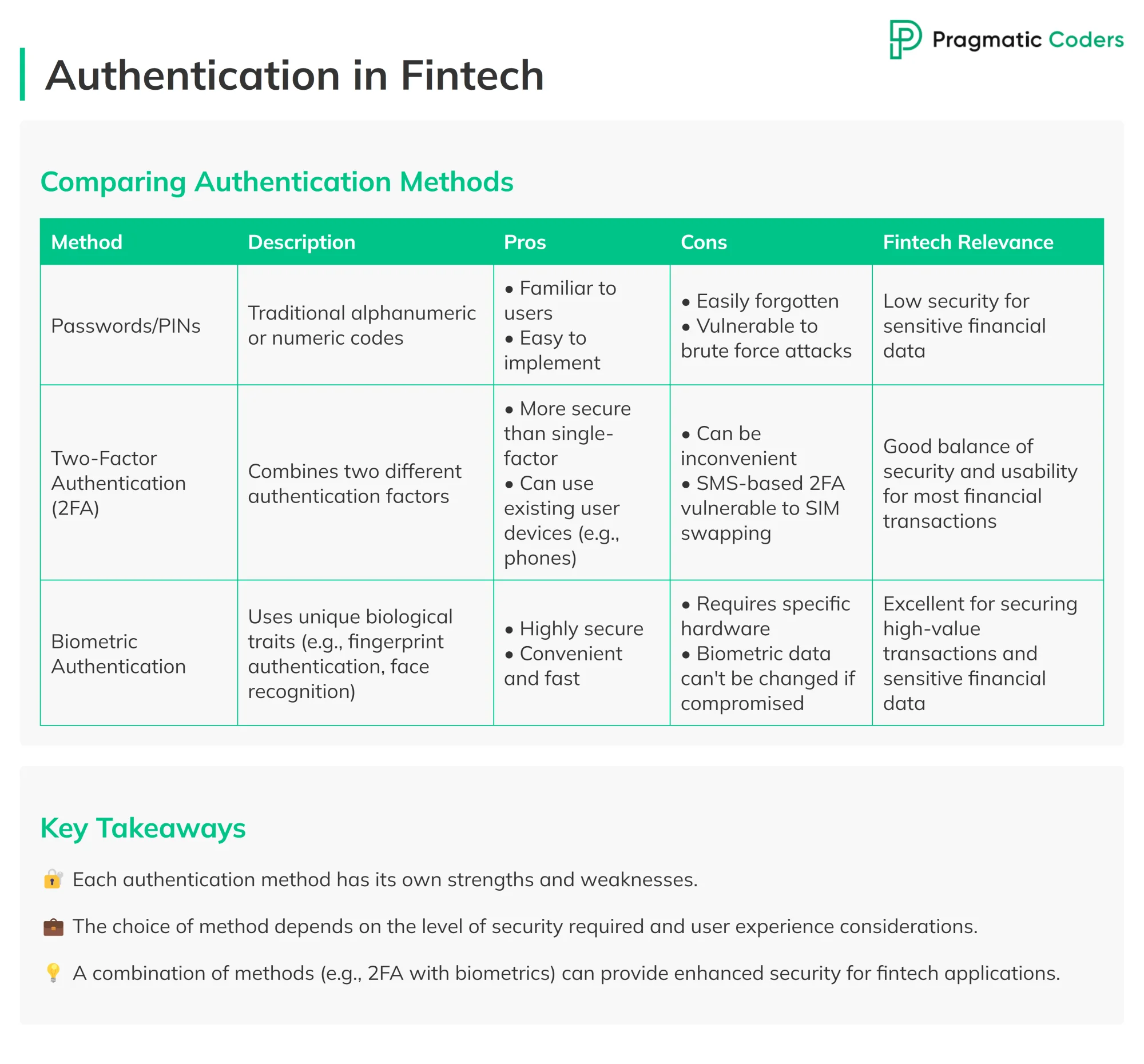
These processes are vital for web apps to control who interacts with customer data, effectively keeping unauthorized individuals out and ensuring users have access to only what they need — no more, no less.
Vigilant Monitoring and Threat Detection: The Invisible Guardians of Cybersecurity
Even with top-notch security in place, some threats linger quietly, looking for an opportunity to cause harm. That’s where vigilant monitoring and threat detection step in as crucial defenders.
Always Watching
Secure web applications often employ advanced monitoring systems to keep an eye on all activities. These systems can analyze large volumes of data, spotting unusual patterns or behavior that might signal an attempted breach.
Acting Fast: Sound the Alarms!
When threats are detected early, businesses can move quickly to address them, minimizing the damage from potential breaches. By using automatic alerts, companies can ensure they respond swiftly to any issues.
Incorporating artificial intelligence and machine learning can boost these capabilities, as these technologies can learn from past incidents and anticipate future risks. With technology advancing rapidly, using these innovations is essential for building a robust shield around precious customer data.
Regular Security Audits: Why It’s Essential to Stay Prepared
Think of security audits like those regular car check-ups that seem to happen at the most inconvenient times.

They might be a hassle, but they’re essential. Conducting regular security audits for web applications is crucial because it lets businesses evaluate their current security stance, spot weaknesses, and update protocols as needed.
The Audit Essentials
An effective security audit covers various aspects, from testing how strong the encryption is to ensuring solid authentication and monitoring processes. To truly understand potential vulnerabilities, businesses should involve both their internal teams and outside security experts.
A Promise to Keep Protecting
Security audits shouldn’t be a one-off task. In today’s digital world, where new threats constantly emerge, continuous audits are vital.
By maintaining an ongoing cycle of reviewing and improving security measures, businesses can offer robust protection for sensitive customer data and demonstrate their dedication to privacy.
In Conclusion
Secure web applications are essential for protecting data. By using a combination of encryption, authentication, monitoring, and regular audits, businesses can create strong defenses to keep customer information safe.
As threats change, so too should our security strategies — always staying ahead to ensure our customers’ trust and loyalty


